It often happens that developers leave a lot of useful information on public repositories.
For example
Sometimes you can find access keys or authorization tokens. One such resource is “github.com”. The majority of developers and employees have an account on it. Therefore, in this article, I will tell you what tools exist and what you can find.
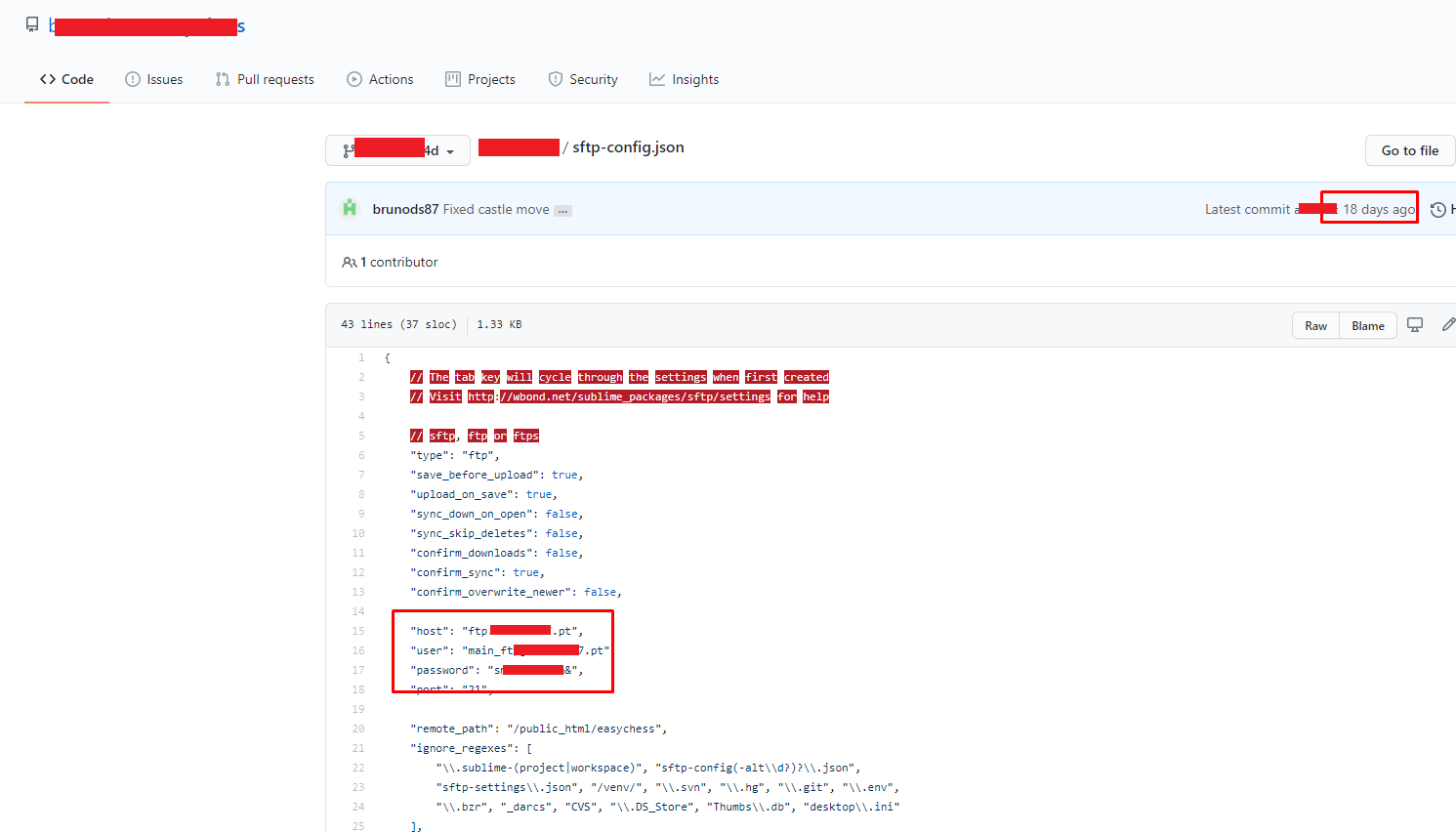
The sftp-config.json file is used by the SFTP plugin in the Sublime editor. It is designed for file transfers, including over SSH. Thus, the host and the access data can be found. filename: sftp-config.json password
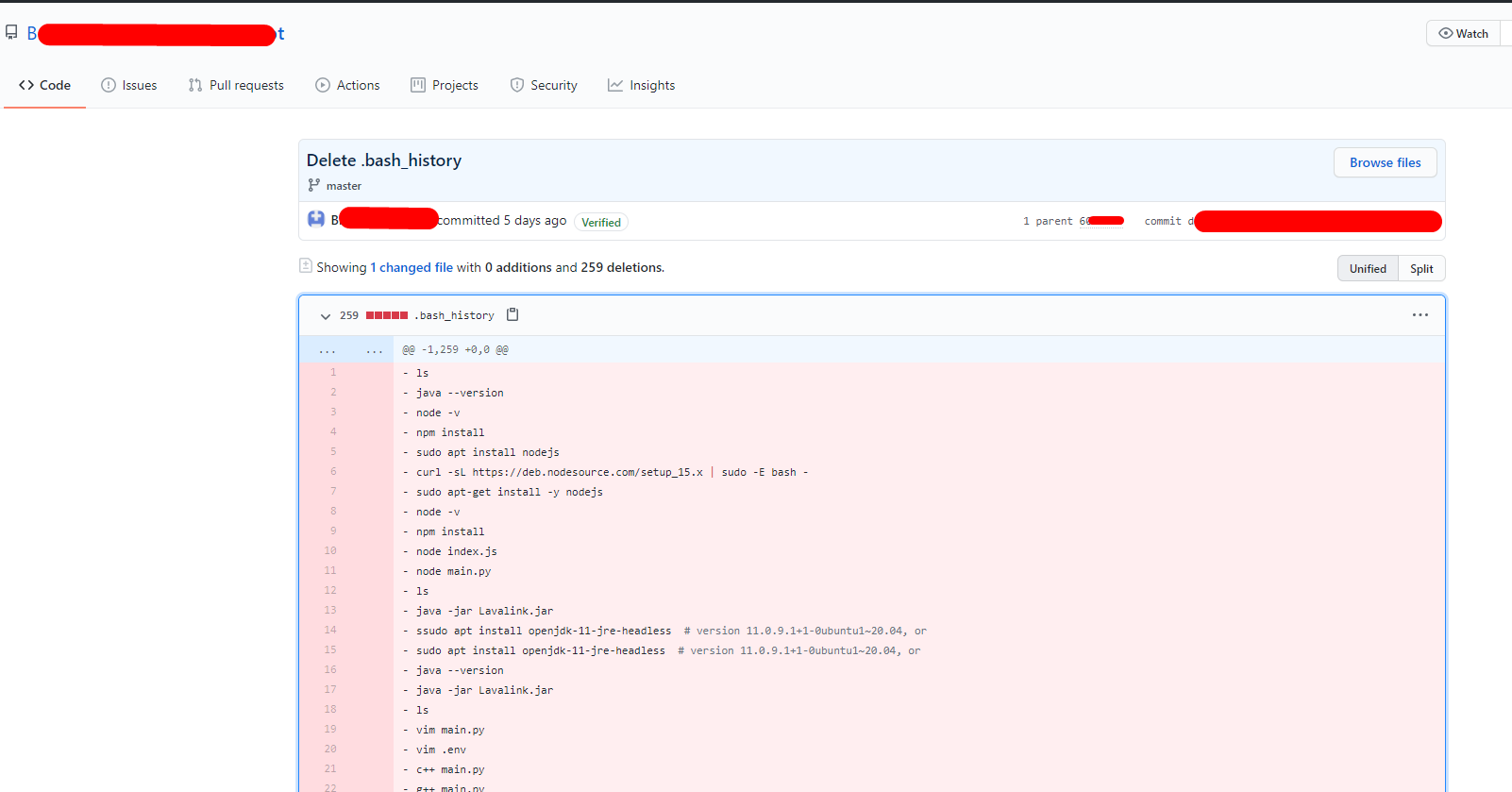
There is another good way to view a list of previously entered commands in bash is the history command. By default, it lists the commands stored in history. By default, everything is written to the ~ / .bash_history file, and its size is 500 commands.
filename: .bash_history
In addition, in the repository, you can find popular dorks, as well as a brief installation help and simple commands. The utility finds results for you for queries that are in the root file.
GithubHunter.py
Allows you to search for keywords and payloads. As a result, you can get a database with queries and found keywords.
gitleaks.py
This utility allows you to find vulnerabilities and credits (login data — username and password) in a specific repository. If you have a website and it has an unloaded project, you can run this utility for known vulnerabilities and weaknesses.
Conclusion
You need to closely monitor the developers. They leave a lot of “bread” for attackers. These can be passwords, configs, different API keys, command histories, etc. Depending on what you need, you can always find it.
Open-source, cloud-based code repositories like GitHub are essentials for developers and software engineers to deploy their code more effectively. But such public platforms are goldmines for hackers and cyber criminals to get hold of sensitive code, access keys, and technical information.
One way to avoid data exposure is to beat the hackers into their own game.
Use a threat surface monitoring tool to scan cross code repositories, pastes sites, and forums and detect the exposed or publicly available data. With a threat surface monitoring tool, you can get the deepest visibility into your data leaks, uncover the risk, and take agile actions.
