It often happens that some website subdomains are underdeveloped. Those websites contain a lot of useful information. We can easily enumerate the subdomain by using the Recon-ng tool. This blog will show you how to extract the subdomain that is publicly available and how to Bruteforce the subdomain.
Installation
$ apt update && apt install git
$ git clone https://LaNMaSteR53@bitbucket.org/LaNMaSteR53/recon-ng.git
$ cd recon-ng
$ pip install -r REQUIREMENTS
Launch.
$ ./recon-ng — no-check
The code:
back Exits the current context
dashboard Displays a summary of activity
db Interfaces with the workspace’s database
exit Exits the framework
help Displays this menu
index Creates a module index (dev only)
keys Manage third-party resource credentials
marketplace Interfaces with the module marketplace
modules Interfaces with installed modules
options Manage the current context options
pdb Starts a Python Debugger session (dev only)
script Records and executes command scripts
shell Executes shell commands
show Shows various framework items
snapshots Manage workspace snapshots
spool Spools output to a file
workspaces Manage workspaces
Enough with the commands, let’s go to the framework itself.
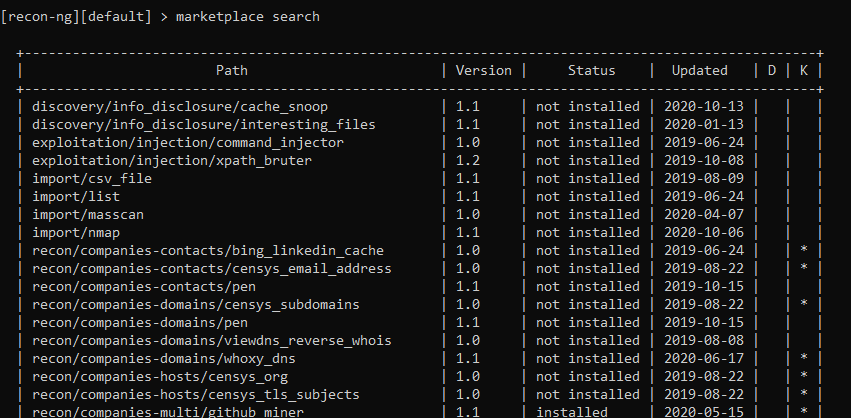
To Search Module in Recon-ng:
[recon-ng][default] > marketplace search
To Install the Module in Recon-ng:
[recon-ng][default] > marketplace install hackertarget
To Select the Module :
[recon-ng][default] > modules load hackertarget
So, let’s select some modules.
First, let’s display the entire list with the “modules search” command. We can immediately see a huge list of modules, everything you need. Let’s use the hacker target module as an example. This module will display the site subdomains and their IP addresses. We select it with the following command: Let’s see the options that we can give it.
The code:
[recon-ng][default] > modules load hackertarget
[recon-ng][default][hackertarget] > info
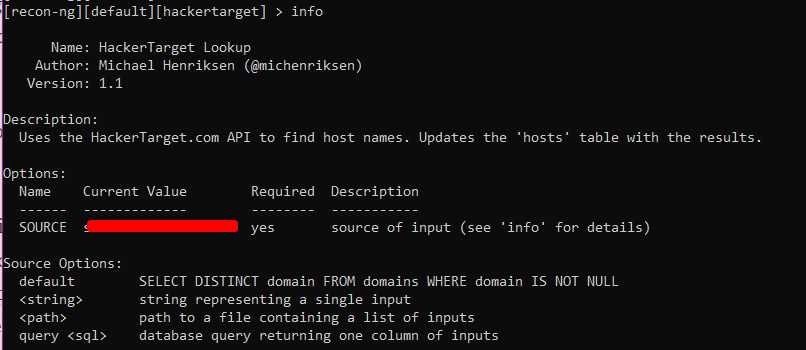
The choice of options is not great, you just need to indicate your goal. Note that for each parameter there is a Required column indicating that the parameter is required. Also, for each parameter, there is a short description in English in the Description column.
Install SOURCE on site.com with the following command:
[recon-ng][default][hackertarget] > options set SOURCE site.com
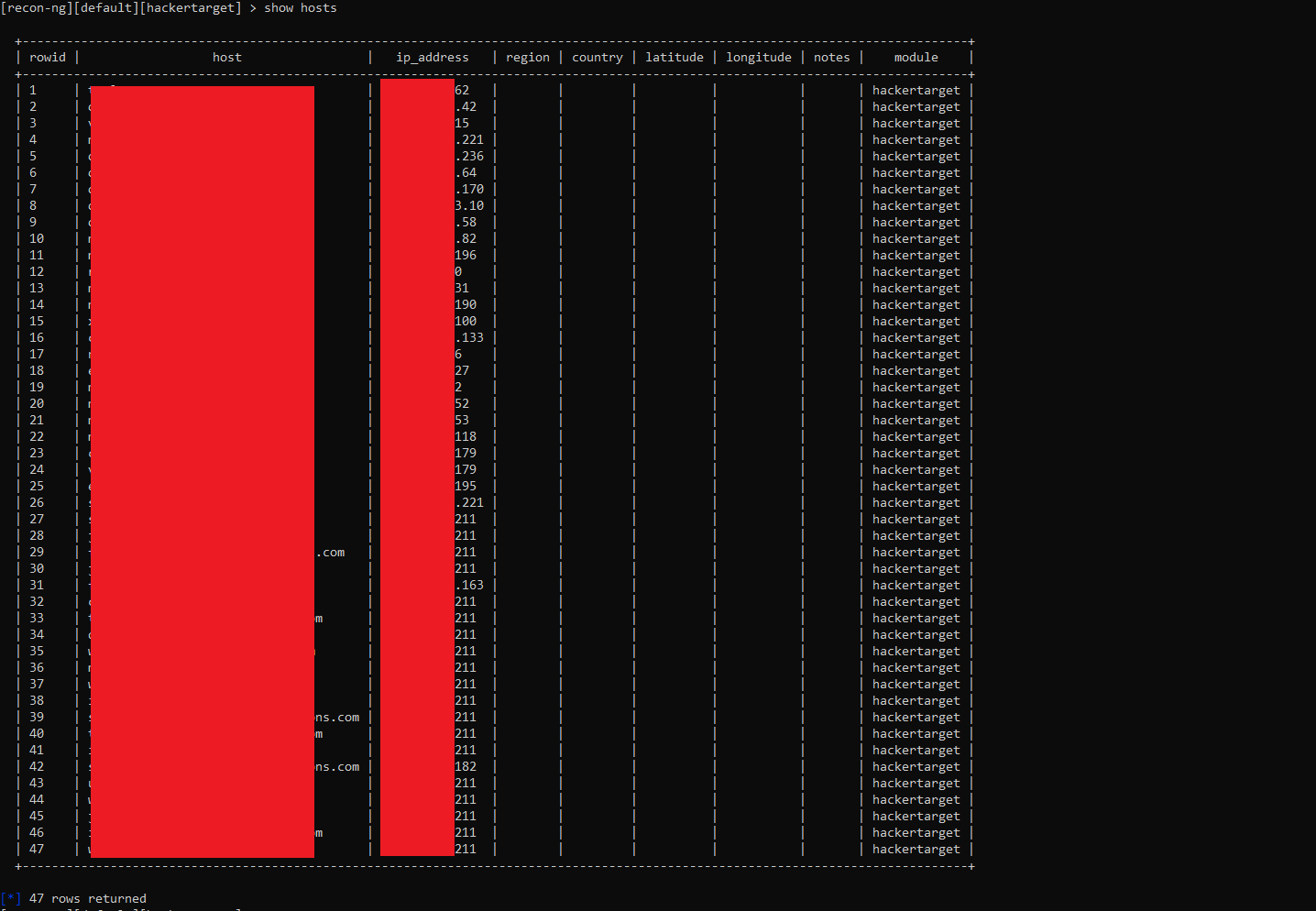
After filling in all the required parameters, you can start the work with the run command. This is the output if you are using the hackertarget module More precisely, not quite the same. You will have a slightly different one. I started it a second time, so there are no new hosts, and you will have new hosts, respectively. To find subdomains and their IP addresses, you can use the recon / domains-hosts / hackertarget module.
To view the hosts in the Recon-ng:
[recon-ng][default][hackertarget] > show hosts
If you think you have not found all domains with the hackertarget module, then you can use the recon / domains-hosts / brute_hosts
module. This module brute -forces hosts.
The code:
marketplace install recon/domains-hosts/brute_hosts
modules load recon/domains-hosts/brute_hosts
options set SOURCE site.com
options set WORDLIST /path/to/your/hostnames.txt
run
options unset SOURCE
To clear the hosts table:
[recon-ng][default] >db query DELETE FROM hosts
Conclusion
Website is the digital mouthpiece and ambassador of your business. If hackers can clone your website domain or take hold of it, they can tarnish the business reputation and cripple the operation quickly.
Traditional security programs focus on protecting assets like websites by safeguarding data stores. However, against the relentless and motivated hackers, this is certainly not enough. Business needs to know what data is already exposed and where to quickly plan the next set of security.
We recommend using an external threat attack surface monitoring tool to scan across the public, dark, and deep web to detect the exposed data, gain maximum visibility into the data leaks, uncover the risk and take agile actions.
