What happened?
A security researcher found the information of 35 million credit card users from an attack on Indian payment gateway, which handles payment for many online marketplaces including Amazon has got leaked on dark web.
Currently, a hacker is selling 365 million user records and that includes Juspay. The threat actors demand $8,000 USD in Bitcoin in exchange for access to the juspay database.
The researcher has published the details on the twitter along with screenshots of dumped data.
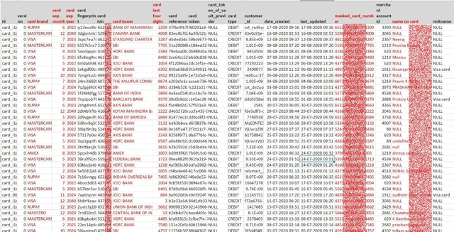
What got leaked?
According to the researcher, the data that got leaked are mentioned below:
- Card numbers (Last four digits & Full masked numbers)
- Expiry date
- The name on the card
- Phone Numbers
- Email Address
- Order information, etc
Juspay’s response on this breach
On August 18, 2020, Juspay identified an unauthorized activity. The company was alerted early in the morning. According to an official statement issued by Juspay, the unusual activity was observed in one of its data stores. “Threat actors abused an old Amazon Web Services (AWS) key to gain unauthorized access. We trigger an automated security alert after a sudden system resources usage”.
Juspay security teams tracked the intrusion and terminated the illegitimate access. The company refreshed the API keys and invalidated the old keys. Other mitigation measures included enforcing 2FA authentication for all tools, adding threat- monitoring. Juspay hack is another example of the importance of implementing two factor authentication (2FA) methods in payment platforms.
Juspay used a delayed approach and the company is constantly trying to downplay this incident. The time between the breach and its public disclosure is certainly critical for the cyber security fraternity. Juspay, although informed its partners it didn’t reveal details of the breach to the public until the security researcher discovered the data dump.
What’s the best security strategy against such focused cyber-attacks?
The cyber-crime landscape is evolving so fast that it’s a matter of time for a hacker to invade and exfiltrate business sensitive data. If they can’t directly infiltrate the business, they are attacking through third parties.
Traditional security strategies are proving insufficient against targeted attacks.
Sumeru recommends the below steps:
- Monitor your external attack surface continuously Monitor partners/third party vendors
- Regular Threat Hunting activity
- Continuous Red Team assessment
For over 20 years, Sumeru is helping businesses to prevent breaches, simulate attacks, monitor security, stay compliant and get secured with 40+ security offerings.
Reach out to at hello@sumerusolutions.com us to know more.
