Amazon s3 has a simple web services interface that can be used to store and retrieve an ‘n’ number of data, at any time from anywhere on the web. Whenever we create any s3 bucket on AWS we will have to be keen about the security access of the bucket too. This is due to the fact that once an s3 bucket is created without any controls, the confidential data that are uploaded in the s3 bucket may get exposed to hackers. By default, s3 buckets are not public in the AWS services but are mostly due to the configuration part while creating the bucket.
Let’s see how some of the basic misconfigurations can be avoided when you create an s3 bucket.
Whenever an s3 bucket is created, make sure that the ‘Block all public access’ settings is not “Off”. There could be scenarios though when there is a static website in the bucket and it doesn’t contain any confidential data, then the public access options can be turned “Off”. If the bucket is public then anyone can access the objects which are uploaded within the bucket.
Bucket Name >>— Permissions >>— “On” Block all public access >>-- Save

Another common flaw is when the ACL permissions are not handled properly.
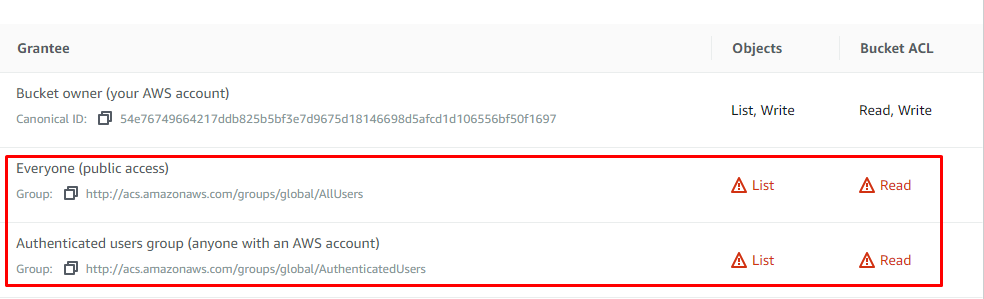
Make sure to disable all these options once the bucket is created. When the list, read options are enabled your objects can be accessed by anyone through command-line access.
Bucket Name >>-- Properties >>-- Access control list >>-- Disable List , Read >>-- Save
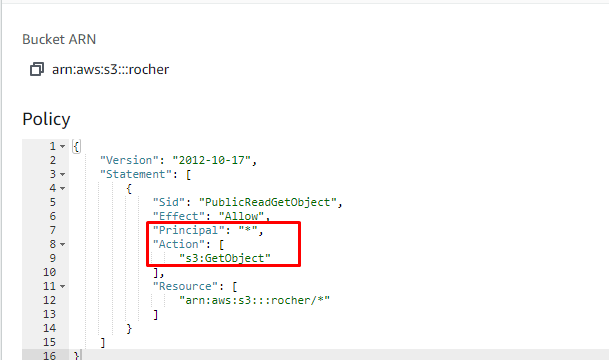
It is a good practice to use a policy within the bucket, but when any policy is created for the bucket check if principal and Action options are given properly.
In action, if the “*” wildcard option is given it means that anonymous public access is provided to everyone. And if this wildcard option is utilized with the action part as “s3:GetObject”, then anyone can get the object from the bucket.
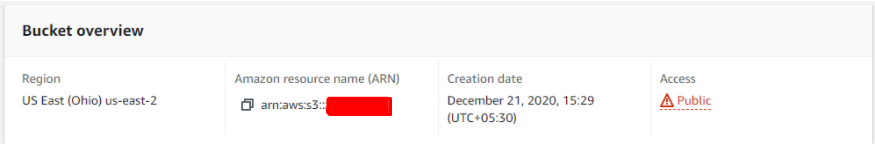
If the bucket is public then various exploits can be carried out.
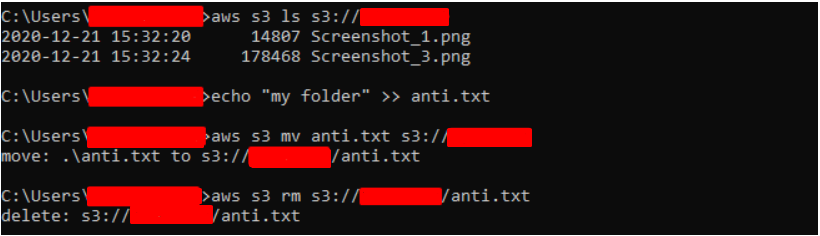
The following commands can be used to list, move, and delete the objects once public access is enabled for the bucket.
aws s3 ls s3://<bucket name>
aws s3 mv file name s3://<bucket name>
aws s3 rm s3://<bucket name>/<file name>
This blog gives some basic s3 bucket flaws which occur whenever an s3 bucket is created and we will see some more in the upcoming posts.
