General Info:-
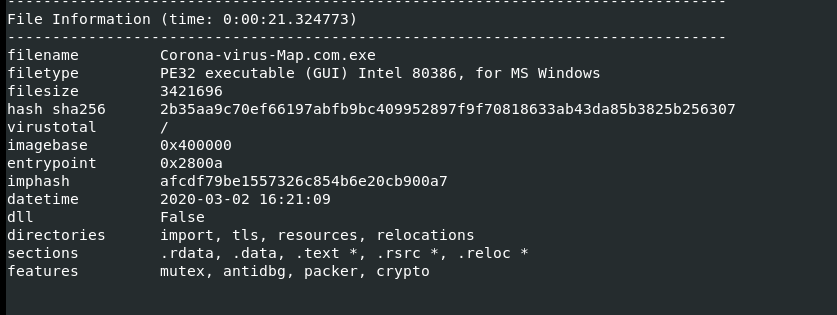
We are using Remnux Linux and windows 10 machine for the analysis, so our first step is to find out which type of malware it is using Peframe tool
And then find entropy value and Characteristics using Peframe.exe in windows Analysis (entropy value 7=>8 ) some data or process are inside the malware
Trigger the Corona-virus-Map.com.exe in a sandbox windows machine and keep the Wireshark and Procmon ready to analyze it in the background. Analyze the processor id, tree structure, modified file path, files dropped.
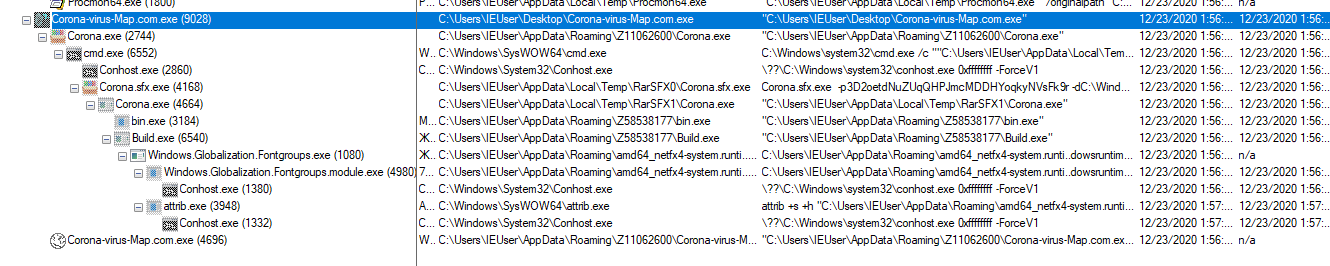
here you can see some suspicious executions, also you can find some of the dropped files like windows.Globalization.Fontgroup.exe

Also, we can see a compressed file and once you extract it, we can see the following information
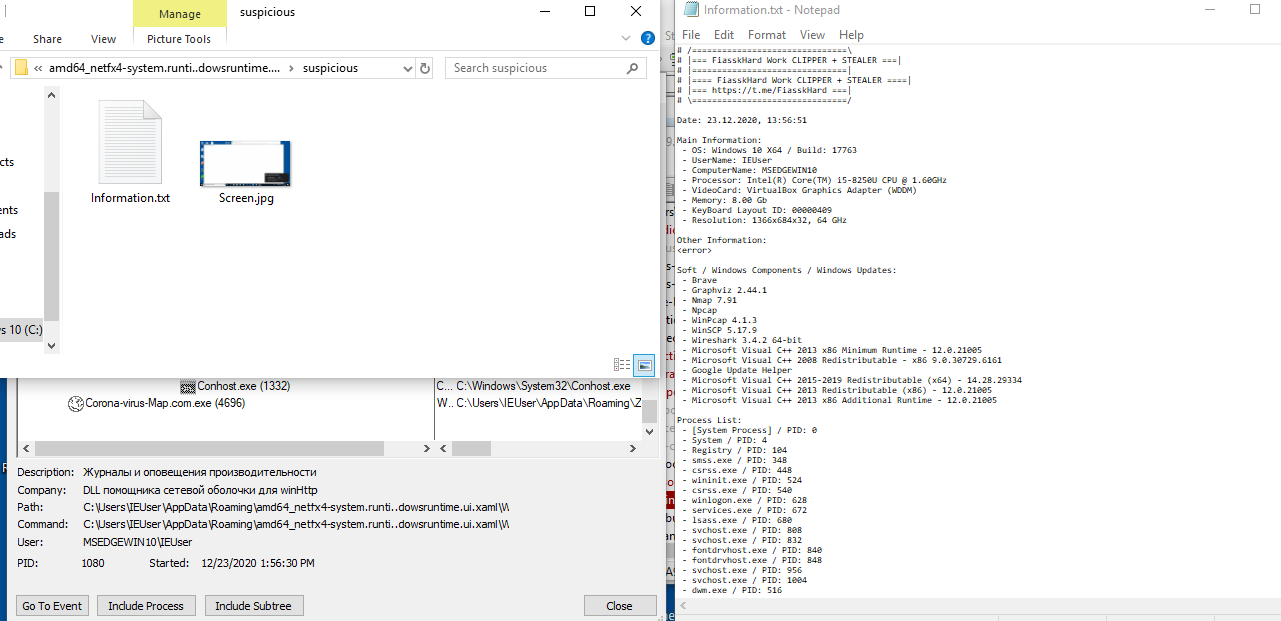
YARA rules are used to look for that code along with some of the malware’s functions and features.
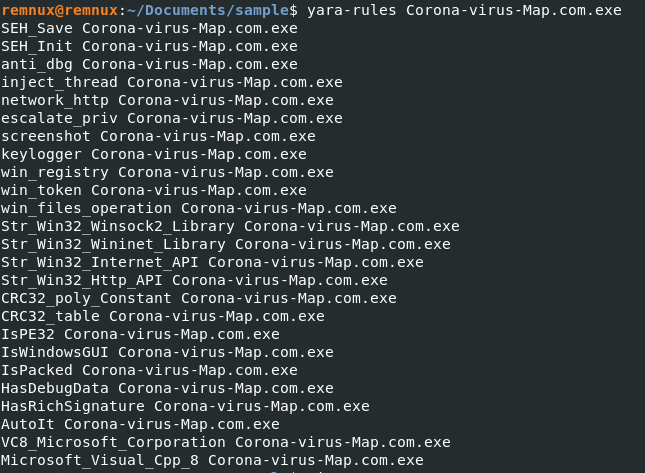
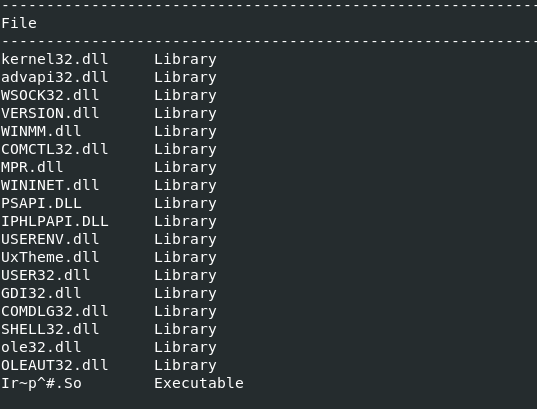
in the Peframe tool, we are able to get what is present in the DLL file
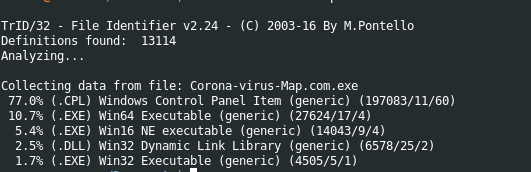
using the TRID tool we can find collected data Info
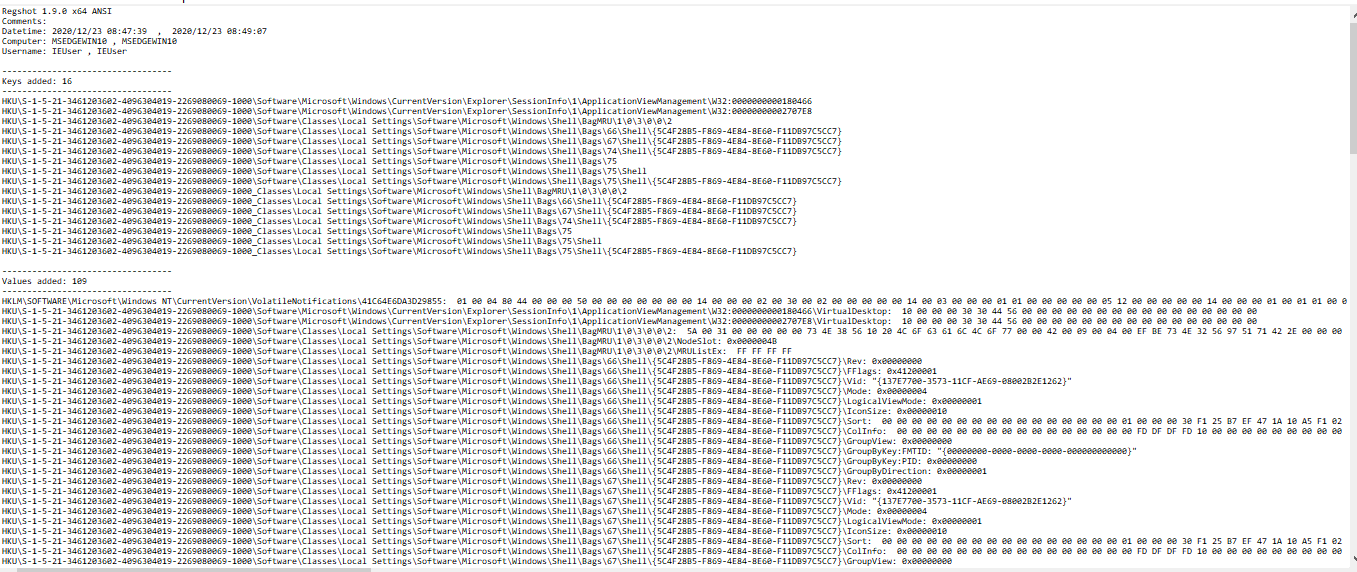
And We are using regshot to find out which files are affected, added, modified, registry modified information can be obtained.
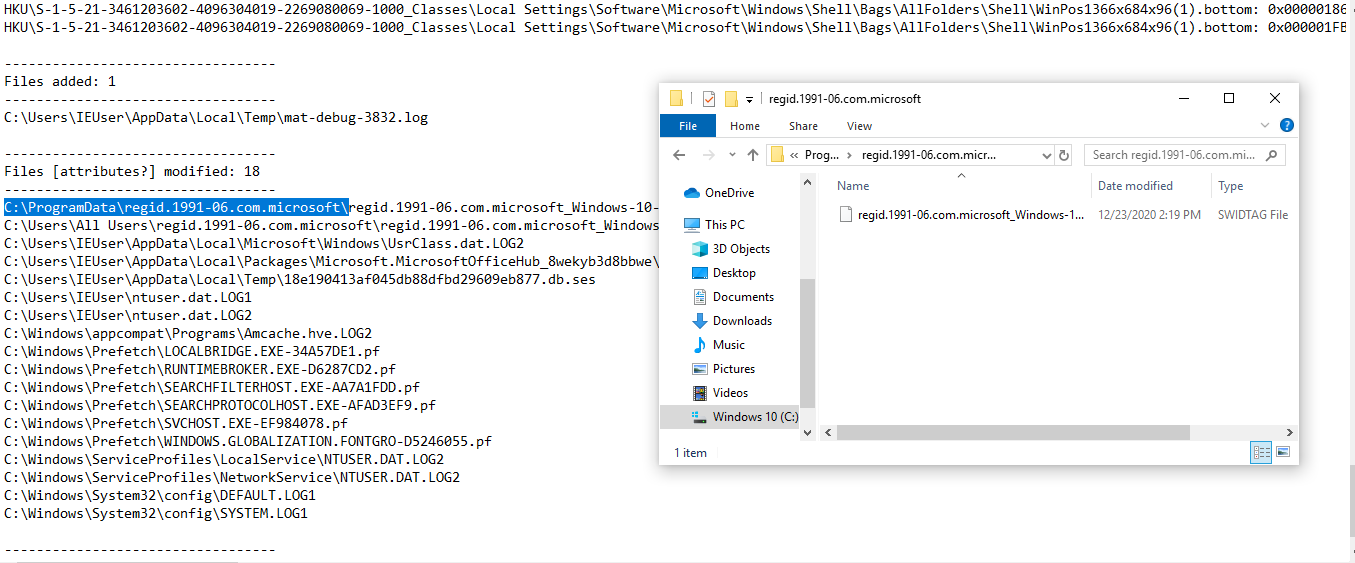
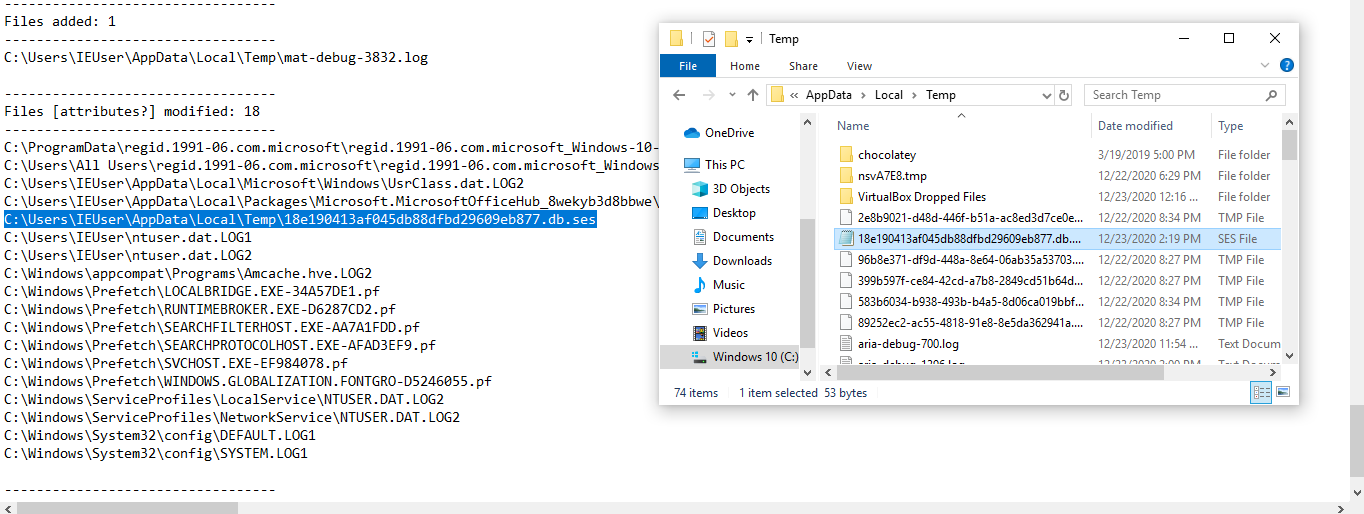
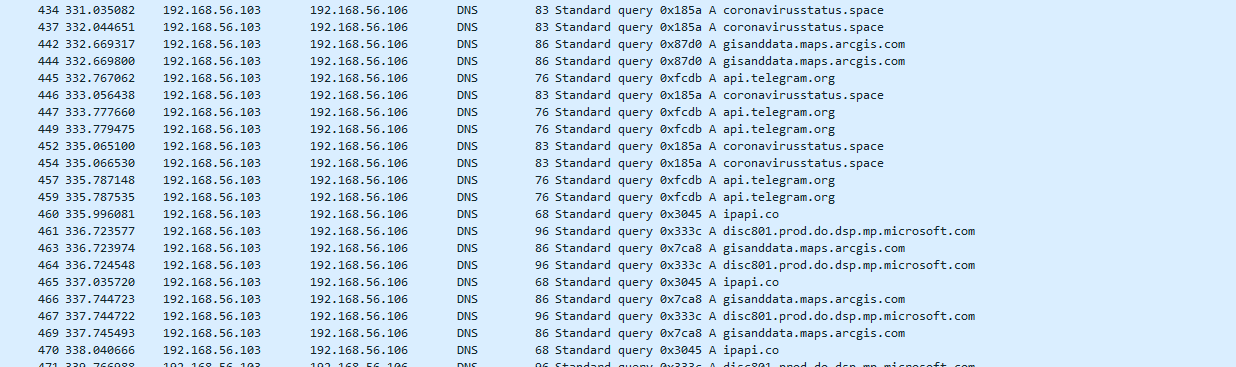
And finally, this data is through the breakpoints DNS
gisanddata.maps.arcgis.com
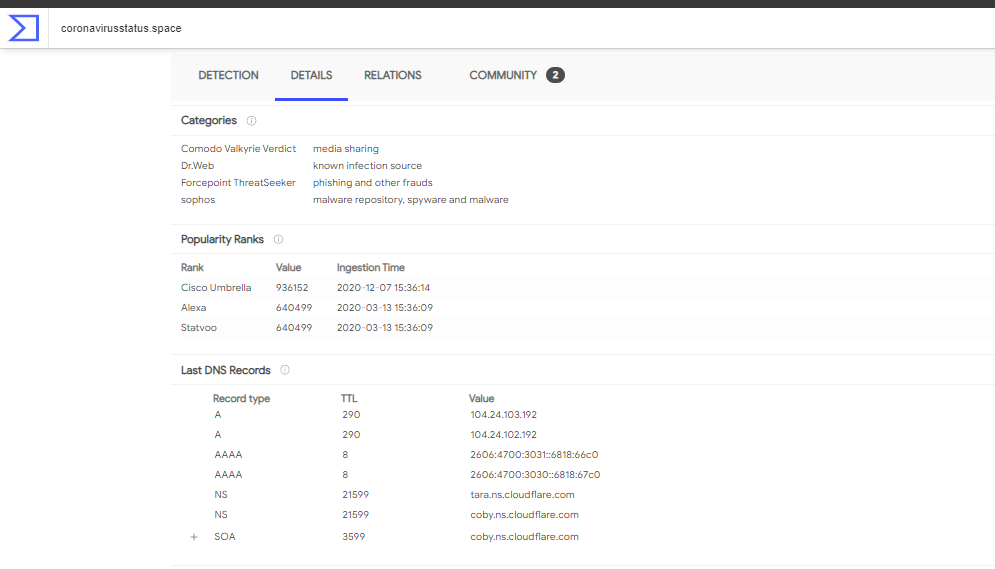
coronavirusstatus.space
api.telegram.org
ipapi.co
js.arcgis.com
Note:- This lab setup in host-only adapter internally reaching with two os flavors (LINUX, WINDOWS)
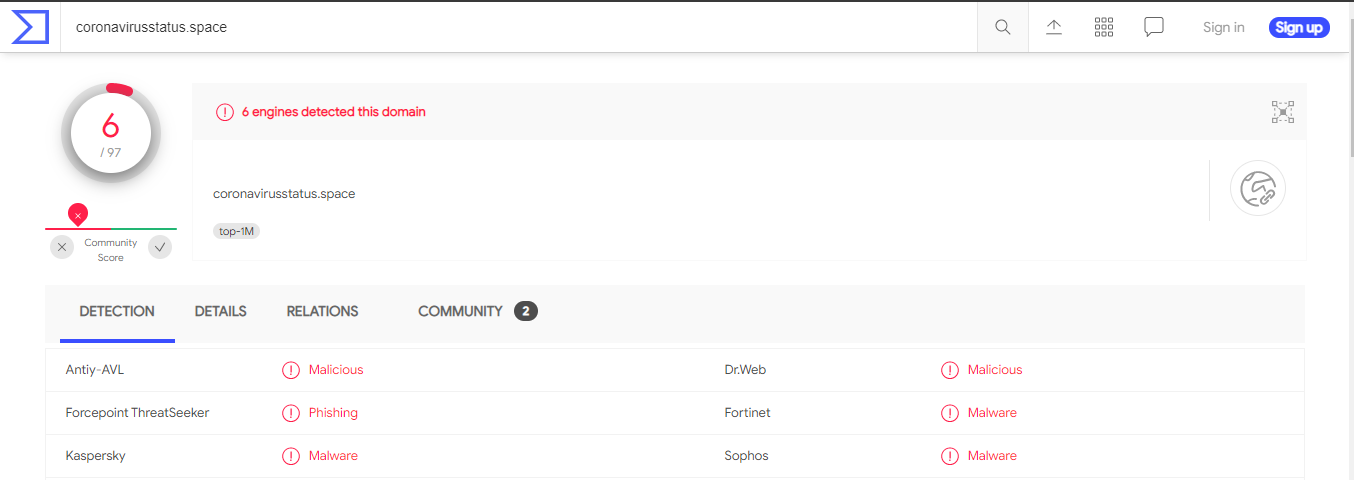
Just checking for coronavirusstatus.space in virustotal is the most vulnerable website.
Today, organizations spend significant money securing IT assets but forget about the internet. It’s so disappointing to see even the sensitive information and details of COVID-19 is spreading across the internet. Attackers know how to take advantage of the situation.
Sumeru Threat Meter scans the entire public internet to find this information for you and paints a clear picture of what your attack surface looks like on the internet.
It’s like we’re your eyes on the internet. Helping you see what hackers see about you. know more about Sumeru Threat Meter here https://inservice.sumeru.com/threat-meter/ . Want to have a demo of Sumeru Threat Meter, reach out to us now https://inservice.sumeru.com/contact-us/
