Data Storage is growing exponentially and becoming more complex, making it harder to manage, and an even bigger challenge to store. That’s why more organizations are looking for public cloud storage options, such as Azure Storage to get the scalability, durability, maintenance, and accessibility. While the benefits are significant, securing Azure storage accounts require additional focus and responsibility.
What are the misconfigurations in Azure Storage accounts?
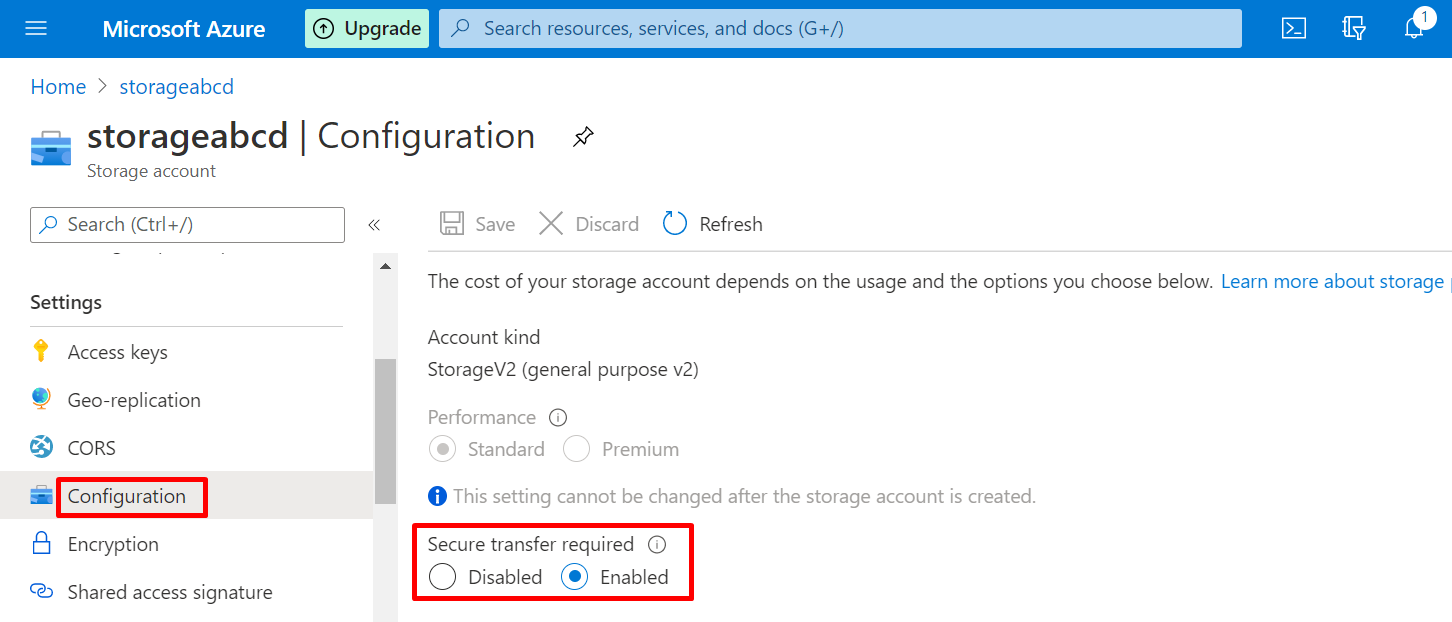
Secure transfer
The “Secure transfer required” feature enhances the security of the storage account by allowing requests only from secure connections. If the secure transfer option is not enabled, you will not ensure that only requests from a secure connection are allowed.
To check the configuration in the portal, select the ‘Configuration’ option available on the left side of the panel.
To check in Azure CLI, Put the following Command.
az storage account show --name <account-name> --query 'enableHttpsTrafficOnly'
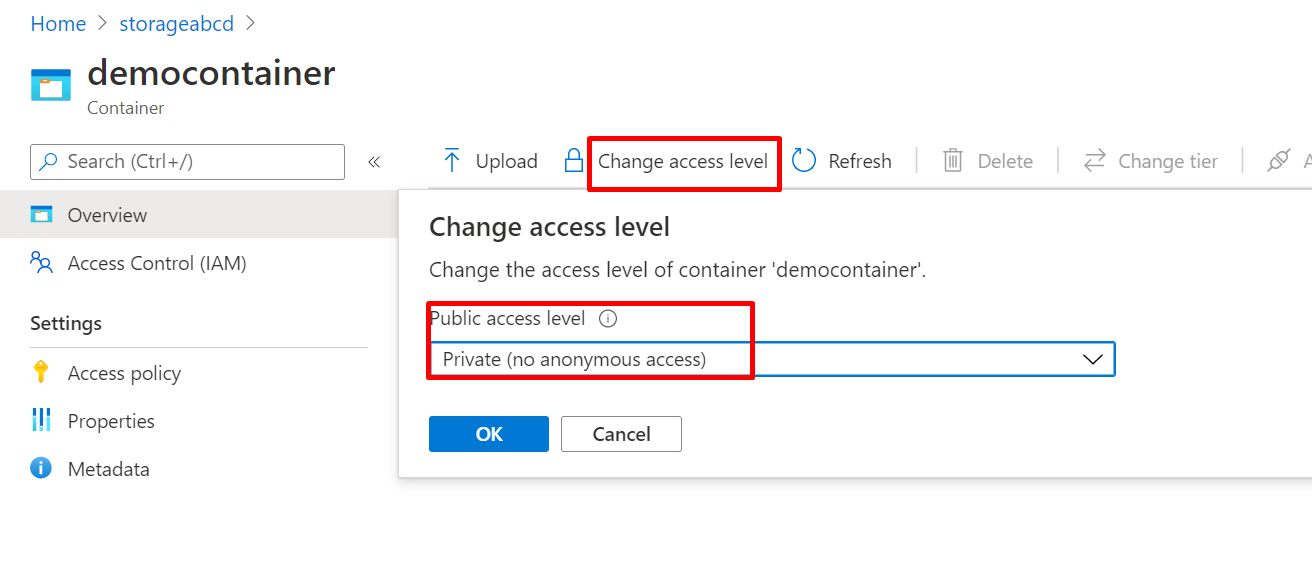
Private access to Blob Containers
Ensure that the “Public access level” configuration setting is set to “Private (no anonymous access)” for all blob containers in the storage account in order to block anonymous access to these Microsoft Azure resources.
To check if anonymous access to Azure Storage blob containers in the portal, select the blob and click change access level and make it into Private.
To check in Azure CLI,
az storage container show --name <container-name> --account-name <account-name> --query 'properties.publicAccess'
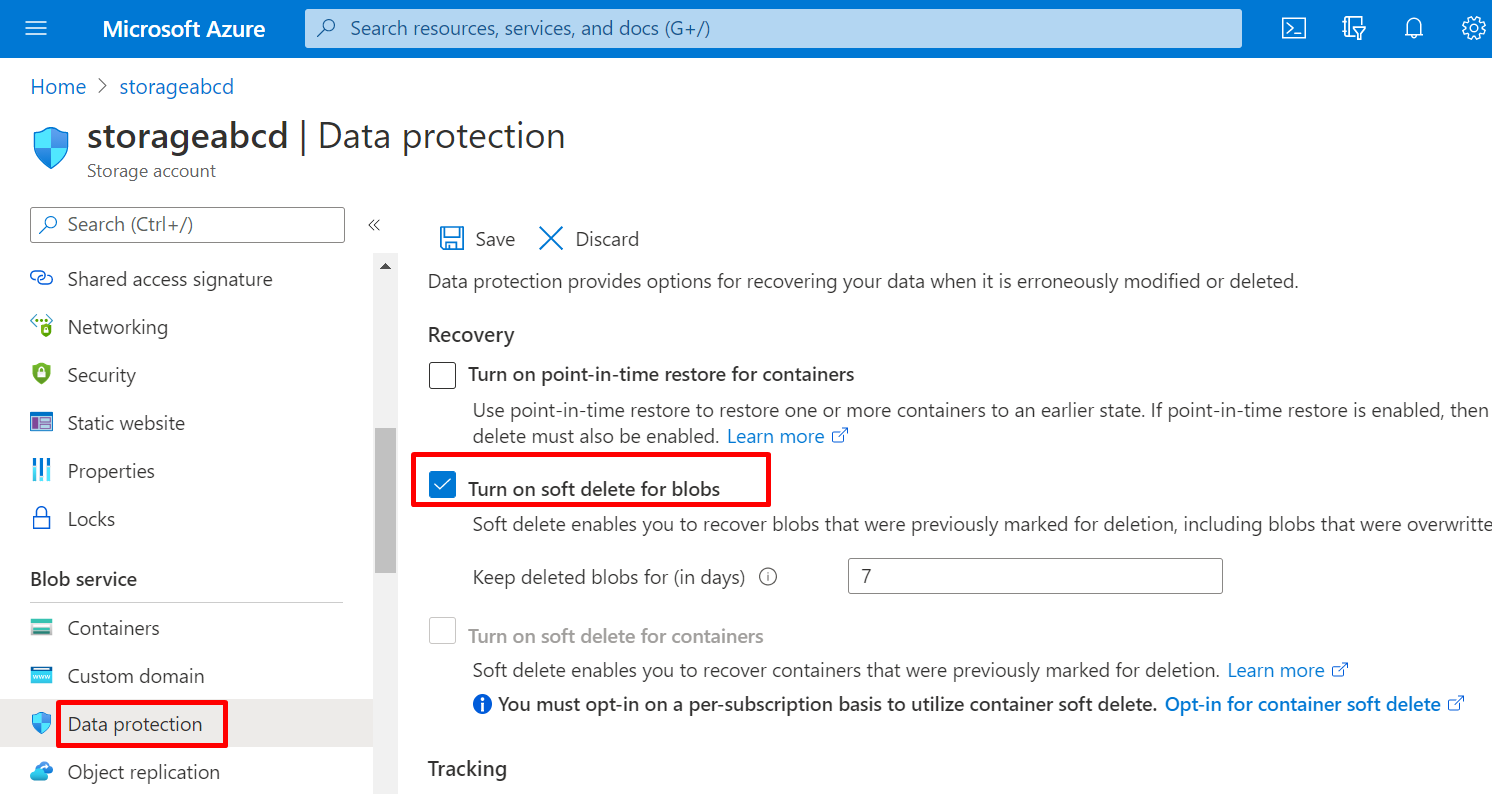
Enable Soft Delete
Ensure that the Soft Delete feature is enabled for all Microsoft Azure Storage blob objects (blobs and snapshots). Soft Delete enables to save and recover blob data in case Azure Storage blobs or blob snapshots are deleted.
To check-in portal, Goto Data protection ->Turn on soft delete for blobs
To check in Azure CLI,
az storage blob service-properties delete-policy show --account-name <account-name> --query 'enabled'
If it returns the requested configuration status as true, then it is enabled. (false for disabled)
Restrict Default Network Access for Storage Accounts
Restricting default network access helps to provide a new layer of security since storage accounts accept connections from clients on any network. To limit access to selected networks, the default action must be changed.
To check it in Azure CLI,
az storage account show --name <account-name> --query 'networkRuleSet.defaultAction'
If the command output returns “Allow”, all networks, including the Internet, can access the selected Azure Storage account, therefore the default network access configuration is not compliant.
Limit Storage Account Access by IP Address
Ensure that the access to Microsoft Azure Storage blobs, files, tables, and queues is limited only to a specific (trusted) public IP address and/or IP address range in order to protect data against unauthorized access.
To check it in Azure CLI,
az storage account show --name <account-name> --query 'networkRuleSet.ipRules[?(action==`Allow`)].ipAddressOrRange'
The command output should return the list with all the IPv4 addresses allowed to access the storage account.
This is how the configurations have to be made securely in the azure storage account.
Secure configuration is important to ensure the cloud infra is well protected. To know more about our security services, solutions, visit https://inservice.sumeru.com/cyber-security/ Got any questions for us? Reach out today.
